TECHNOLOGY & SECURITY
I2D2 is
data-responsible.
Our processes and analysis remain objective and honest. We have a comprehensive data governance plan to mitigate risks and to protect Iowan’s information — while we provide our state’s leaders with whole-picture insights to better support Iowan’s needs.
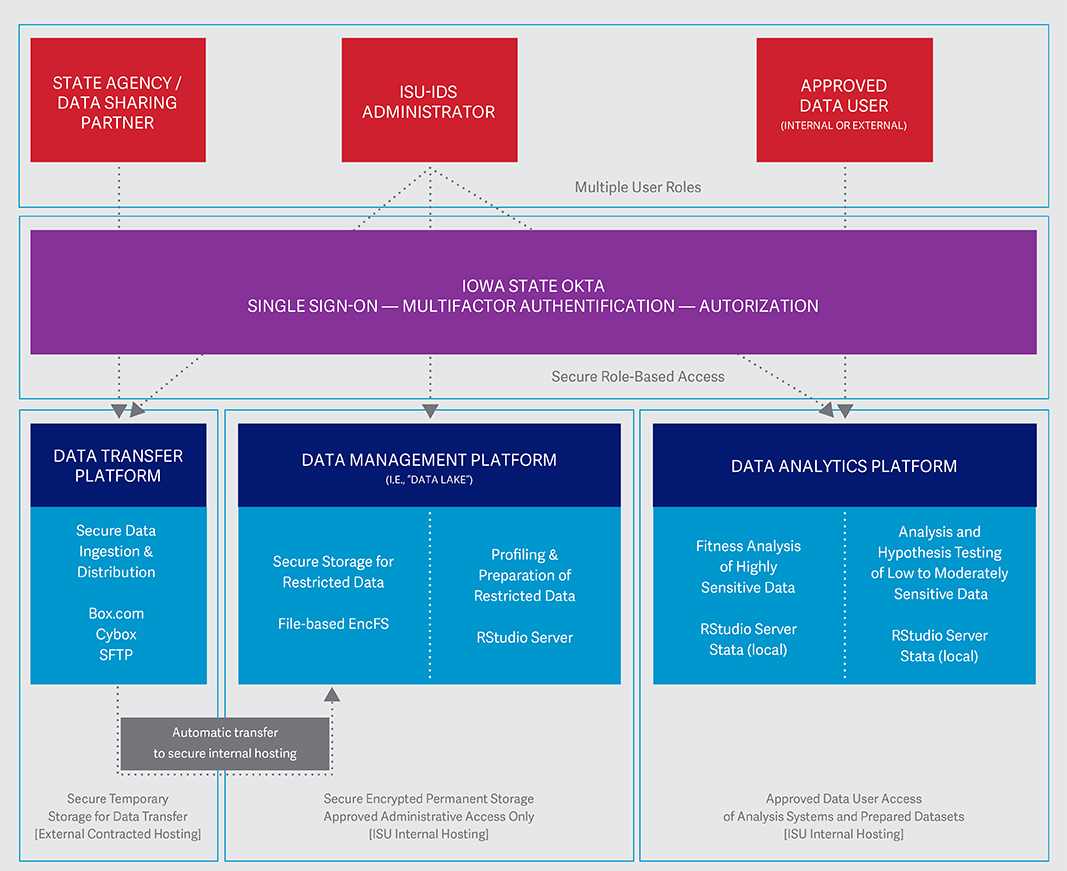
I2D2 technology approach
Data Transfer Platform (Classification = Restricted)
The Data Transfer Platform is used to securely transmit data from partners. We use a secure data technology that is compliant with HIPPA and HIETCH and accredited at the Department of Defense Cloud Computing Security Requirements Guide Impact Level 4 Authorization. Each agency that provides data to I2D2 will have their own data portal with user-defined roles including one-way data transfer and time-limited access portals for data sharing.
Data Management Platform (Classification = Restricted)
The Data Management Platform has three key functions:
To securely retrieve data from the Data Transfer Platform.
To securely store the data and provide a platform for profiling, preparation, and project-authorized integration.
To securely transmit anonymized data to the Data Analytics Platform.
The retrieval of uploaded data is automated to load into the I2D2 data server, which has highly restricted access to a small number of individuals who will have approved access to profile and prepare the data for use in the analytics platform.
Data Analytics Platform (Classification = High + Moderate)
The Data Analytics Platform has three key functions:
To securely store highly sensitive data for fitness analysis.
To securely store low-to-moderately sensitive data for analysis and hypothesis testing.
To house all data products produced by authorized users for verification by system administrators before release to authorized users.
The Data Analytics Platform is made up of a separate server from the Management Platform dedicated for use by researchers to analyze the data. We will minimize access to these datasets and related data products and require all researchers to have an ISU identity and login through our single sign-on, multi-factor OKTA authentication system before getting access. Data analysis reports based on the datasets may be extracted and shared with researchers with compliance authorization by I2D2 system administrators.
I2D2 Information Security
Access Control
All access is limited and minimized to private data and systems that process it, based on business need. Agencies will not be able to view other agency’s data within the I2D2 data transfer platform. Employees within the same agency will not be able to view data uploaded by another employee within the I2D2 data transfer platform.
I2D2 defines individual access, approving and granting authority for each system.
All personnel being considered for access to restricted data must undergo a background check.
I2D2 tracks access requests in an access log, including who grants the access change.
I2D2 requires multi-factor authentication for all access to data sets classified as Restricted using OKTA.
I2D2 requires multi-factor authentication for all administrative access to servers in this system by limiting system access to only VPN IP addresses (VPN requires MFA).
The systems require complex passwords for all access to restricted data.
I2D2 periodically reviews the personnel who have access to the data management and data analytics platforms to ensure access is still required and appropriate.
All restricted data is encrypted at rest and securely deleted using methods prescribed in NIST SP 800-88.
Security Assessment and Monitoring
The security team at I2D2 is diligent to detecting potential threats by periodically scanning the system and web applications for vulnerabilities. Any identified issues will be brought to the immediate attention of IT. Any vulnerabilities will be mitigated as soon as possible.
The security team monitors internet communications to the system and alerts on connections to known malicious destinations. Additionally, regular activity logs are sent to the central server for forensic evidence standby.
Incident Response
The project team uses the ISU Security Team’s incident response capabilities in the event of a suspected data breach by emailing security@iastate.edu. The ISU Security Team documents and handles incidents according to all applicable laws and statutes. This includes documentation and notification to appropriate officials both inside and outside the university.
Physical Security
All servers (physical or virtual) are stored in secure physical data centers. These data centers employ the following physical security controls:
Secure physical perimeter
Internal segmentation between tenants
Fire safety
HVAC
Identity and access management controls and procedures
Video surveillance
